Table of Contents
1.Introduction:
Information technology (IT) has revolutionized the way we live and work in today’s world From the internet and smartphones to cloud computing and artificial intelligence (AI), the digital age has transformed the way we communicate, access information, and conduct business.
This rapidly evolving field has brought about a range of innovations that have transformed various industries, including healthcare, finance, education, and entertainment. With the constant emergence of new technologies, it is essential to stay updated on the latest
trends and developments in IT. This article will provide an overview of some of the latest trends and innovations in information technology, including the Internet of Things (IoT), AI, cloud computing,blockchain technology, and cyber security. By exploring these topics, we can gain a deeper understanding of how technology is changing the world and shaping our future.
Whether you are a business owner, a student, or a technology enthusiast, this article will provide valuable insights into the latest advancements in IT and the impact they are having on our lives. So let’s dive in and discover the exciting world of information technology.

2.The Internet of Things (IoT): Connecting Everything and Everyone
Overview of IoT technology and applications
The Internet of Things (IoT) is a system of interconnected devices, sensors, and software that enables communication and data exchange between physical objects, such as appliances, vehicles, and buildings, through the internet. It is a network of smart devices that work together to create a seamless and interconnected system, bringing automation and efficiency to various industries.
IoT technology has numerous applications, including in the areas of healthcare, transportation, manufacturing, and agriculture. In healthcare, for instance, IoT devices can be used to monitor patients remotely, track vital signs, and provide personalized healthcare services. In transportation, IoT technology can be used to optimize traffic flow, reduce congestion, and enhance safety by connecting vehicles and infrastructure.
In manufacturing, IoT devices can improve efficiency and productivity by monitoring equipment performance and predicting maintenance needs. In agriculture, IoT technology can help farmers to optimize crop yield, reduce water usage, and monitor soil conditions.Moreover, IoT devices are becoming more prevalent in homes, with the advent of smart home technology. Smart thermostats, lighting systems, and security cameras are examples of IoT devices that enable homeowners to control and monitor their homes remotely.
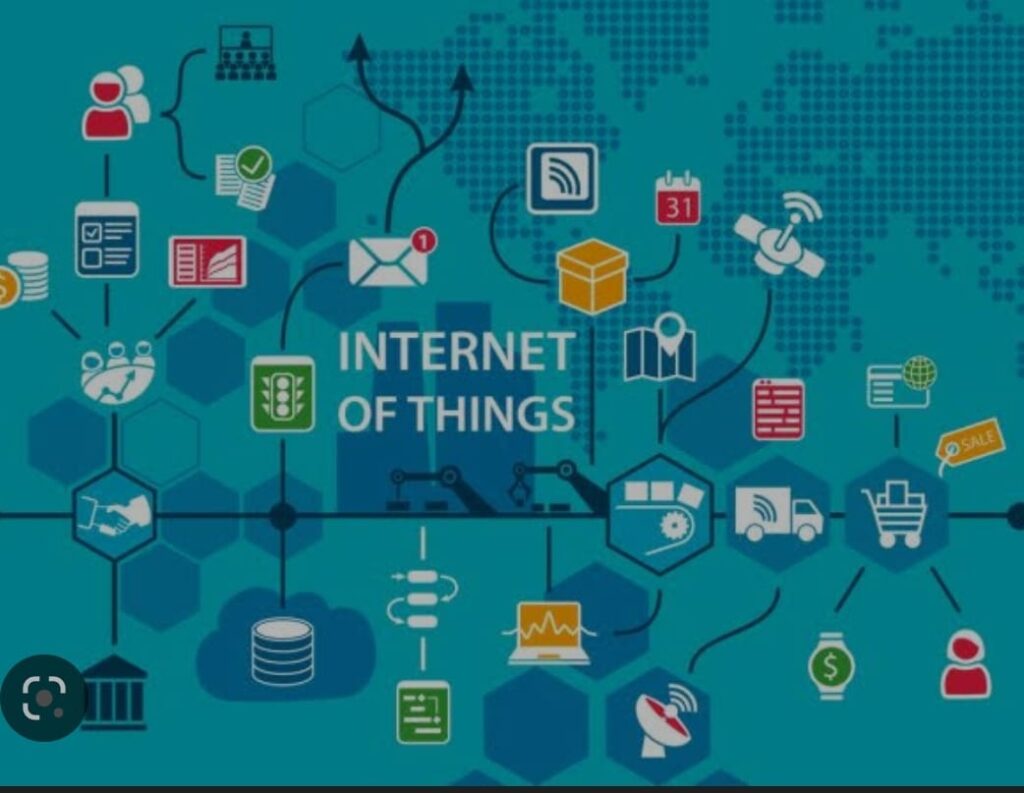
Overall, IoT technology is transforming industries and creating new opportunities for innovation and growth.
Impact of IoT on industries and society
The impact of IoT on industries and society is far-reaching, and its potential is still being explored. Here are some of the ways in which IoT is impacting various industries and society as a whole:
- Increased Efficiency: IoT devices enable automation and optimization of processes, leading to increased efficiency and productivity in various industries.
- Improved Safety: IoT technology is being used to enhance safety in industries such as transportation and healthcare by enabling real-time monitoring of critical systems and early detection of potential issues.
- Better Resource Management: IoT devices can be used to monitor and manage resources such as energy, water, and waste, leading to more efficient and sustainable practices.
- Enhanced Customer Experience: IoT technology is enabling businesses to provide personalized and seamless experiences for their customers, such as personalized healthcare services and tailored recommendations for shopping.
- New Business Models: IoT technology is creating new opportunities for innovation and growth, leading to the emergence of new business models and revenue streams.However, there are also concerns regarding the impact of IoT on privacy and security, as the increasing amount of data being collected by IoT devices creates new vulnerabilities and risks.
Overall, the impact of IoT on industries and society is significant and growing, with the potential to transform the way we live and work. As IoT technology continues to evolve, it is essential to balance the benefits with the risks and ensure that it is used in a way that benefits everyone.
3.Artificial Intelligence (AI): Changing the Way We Work and Live
Explanation of AI and its subfields (e.g., machine learning, natural language processing)
Artificial Intelligence (AI) refers to the development of computer systems that can perform tasks that typically require human intelligence, such as learning, problem-solving, decision-making, perception, and language understanding.

Here are some of the subfields of AI:
- 1.Machine Learning: Machine learning is a subfield of AI that enables computers to learn and improve from experience without being explicitly programmed. It uses algorithms and statistical models to analyze and identify patterns in large datasets, which can then be used to make predictions or decisions.
- 2.Natural Language Processing (NLP): NLP is a subfield of AI that deals with the interaction between computers and human language. It involves developing algorithms and models that can analyze, interpret, and generate human language in a way that is meaningful to humans.
- 3.Computer Vision: Computer Vision is a subfield of AI that enables computers to interpret and understand visual information from the world around them. It involves developing algorithms and models that can analyze and identify objects, people, and other visual data.
- 4.Robotics: Robotics is a subfield of AI that involves the development of intelligent machines that can perceive, reason, and act in the physical world. Robotics combines AI, sensors, and other technologies to create autonomous machines that can perform tasks in a variety of settings.
- 5.Expert Systems: Expert systems are AI programs that can simulate the decision-making abilities of a human expert in a particular field. They use a knowledge base and a set of rules to reason about and solve problems in a specific domain.
- 6.Speech Recognition: Speech recognition is a subfield of AI that involves the development of algorithms and models that can recognize and transcribe spoken language. It is used in applications such as virtual assistants, speech-to-text software, and voice-controlled devices.
- 7.Cognitive Computing: Cognitive computing is a subfield of AI that aims to create intelligent systems that can mimic human thought processes. It involves developing algorithms and models that can reason, learn, and understand natural language in a way that is similar to human cognition.
These subfields of AI are often used in combination to create more complex and intelligent systems, such as self-driving cars, intelligent personal assistants, and medical diagnosis tools.
Examples of AI applications (e.g., autonomous vehicles, chatbots
Here are some examples of AI applications in various fields:
- Autonomous Vehicles: Autonomous vehicles, also known as self-driving cars, use AI technologies such as computer vision, machine learning, and sensors to navigate roads and make decisions.Companies like Tesla, Google, and Uber are working on developing self-driving cars.
- Chatbots: Chatbots are AI-powered programs that can simulate human conversation to answer questions, provide customer support, and assist with various tasks. They are used in customer service, e-commerce, and other industries.
- Image Recognition: AI-powered image recognition systems can analyze images and videos to identify objects, people, and other visual data. They are used in security, healthcare, and other applications.
- Recommendation Systems: Recommendation systems use AI algorithms to analyze user data and suggest products, services, or content based on their preferences and behaviors. They are used in e-commerce, entertainment, and other industries.
- Virtual Assistants: Virtual assistants, such as Siri and Alexa, use AI technologies to understand and respond to user commands and questions. They are used in smart home devices, smartphones, and other applications.
- Fraud Detection: AI-powered fraud detection systems can analyze financial transactions and detect fraudulent activities in real-time. They are used in banking, insurance, and other industries.
- Medical Diagnosis: AI-powered medical diagnosis systems can analyze patient data and suggest diagnoses and treatment plans. They are used in healthcare to improve accuracy and efficiency.
- Personalized Marketing: AI-powered personalized marketing systems can analyze customer data and suggest personalized marketing messages and campaigns. They are used in advertising and marketing to improve customer engagement and conversion rates.
These are just a few examples of the many AI applications that are currently being used and developed.
Ethical considerations of AI
AI is a powerful technology that can have significant impacts on individuals, society, and the environment. As such, there are several ethical considerations that need to be taken into account when developing and deploying AI systems.
- Bias: AI algorithms can perpetuate and even amplify existing biases and discrimination if not designed with care. To mitigate bias, developers should ensure that their models aretrained on diverse and representative data sets, regularly audited and tested for fairness, and monitored for unintended consequences.
- Privacy: AI often relies on collecting and analyzing large amounts of personal data, raising concerns around privacy and data protection. Developers must ensure that AI systems comply with relevant data protection regulations and respect users’ privacy rights.
- Transparency: It can be challenging to understand how AI systems arrive at their decisions, which can be problematic when those decisions impact people’s lives. Developers should strive to make AI systems transparent and explainable, so users can understand how the system works and what factors contributed to its decisions.
- Accountability: AI systems can make mistakes or have unintended consequences, which can be challenging to attribute blame to. Developers and organizations need to establish clear lines of accountability and be responsible for the actions of their AI systems.
- Safety: AI systems can pose physical and cybersecurity risks if not developed with safety in mind. Developers must ensure that their systems do not pose risks to human health and safety, and that they are secure from cyber threats.
- Equity: AI can exacerbate existing social and economic inequalities if not developed with equity in mind. Developers should strive to develop AI systems that promote fairness and equality and address social and economic inequalities.
- Job Displacement: AI systems can automate many tasks that were previously done by humans, potentially leading to job displacement and economic inequality.
- Responsibility: As AI systems become more autonomous, it becomes increasingly difficult to assign responsibility for their actions, raising questions about who is responsible when things go wrong.
These are just a few of the ethical considerations that need to be addressed as AI continues to advance. It is important to approach the development and deployment of AI systems with a thoughtful and critical perspective, and to ensure that these systems are being used in a way that aligns with our values and principles.
4.Cloud Computing: Transforming Business Operations and IT Infrastructure
Definition of cloud computing and its benefits
Cloud computing refers to the delivery of computing resources, such as servers, storage, databases, networking, software, and analytics, over the internet on a pay-for-use basis. Instead of owning and managing physical infrastructure, organizations can use and access resources provided by cloud service providers on demand.

Some of the benefits of cloud computing include:
- Cost savings: Cloud computing eliminates the need for organizations to invest in and maintain their own IT infrastructure, reducing capital expenditures and operational costs.
- Scalability: Cloud computing resources can be quickly and easily scaled up or down to meet changing business needs.
- Flexibility: Cloud computing allows organizations to access computing resources from anywhere with an internet connection, enabling remote work and increasing productivity.
- Security: Cloud service providers often have robust security measures in place, including data encryption and access controls, to protect against cyber threats.
- Collaboration: Cloud computing facilitates collaboration by allowing multiple users to access and work on the same data and applications from different locations.
- Reliability: Cloud service providers often offer high availability and uptime guarantees, reducing the risk of service disruptions.
Overall, cloud computing enables organizations to be more agile, efficient, and innovative by providing flexible access to computing resources without the burden of managing physical infrastructure.
Types of cloud services (e.g., SaaS, PaaS, IaaS)
Cloud computing is a model for delivering computing services, including servers, storage, databases, software, analytics, and more, over the internet. There are three primary types of cloud services:
Cloud computing services can be broadly classified into three categories: Software as a Service (SaaS), Platform as a Service (PaaS), and Infrastructure as a Service (IaaS).
Here’s a brief overview of each of these categories:
- 1.Software as a Service (SaaS): SaaS is a cloud-based software delivery model in which the provider hosts the application and makes it available to customers over the internet. The software is accessible through a web browser or a mobile app, and users can use it on a subscription basis. Examples of SaaS include Google Workspace, Salesforce, Dropbox, and Zoom.
- 2.Platform as a Service (PaaS): PaaS is a cloud computing model in which the provider delivers a platform to the customer, allowing them to develop, run, and manage their own applications without having to worry about the underlying infrastructure. PaaS provides a complete development and deployment environment in the cloud, including programming languages, libraries, and tools. Examples of PaaS include Microsoft Azure, Google App Engine, and Heroku.
- 3.Infrastructure as a Service (IaaS): IaaS is a cloud computing model in which the provider delivers virtualized computing resources over the internet. This includes servers, storage, networking, and other computing resources. Customers can use these resources to run their own applications or services, and can scale up or down as needed. Examples of IaaS include Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform.
Examples of cloud computing in different industries (e.g., healthcare, finance)
Cloud computing has revolutionized the way businesses operate across various industries, and it has become a critical technology for organizations to improve their operational efficiency, reduce costs, and enhance their capabilities. Here are some examples of cloud computing in different industries:
1.Healthcare:
- Cloud computing has enabled healthcare organizations to store, process, and share patient data securely and efficiently. For instance, electronic health record (EHR) systems are widely used in the healthcare industry to digitize patient records, enabling healthcare providers to access critical patient data in real-time from anywhere, and streamline their workflows. Also, healthcare providers can leverage cloud-based telemedicine solutions to provide remote care to patients in different locations.
2.Finance:
- Cloud computing has transformed the way financial services companies manage their data and systems. Financial institutions can leverage cloud-based infrastructure and services to process transactions faster, increase security, and reduce costs. For example, financial services firms can use cloud-based analytics to detect fraud in real-time, allowing them to identify potential issues before they escalate. Also, cloud-based data warehouses are widely used in the finance industry to store large amounts of data, enabling financial institutions to analyze data and gain insights more effectively.
3.Education:
- Cloud computing has revolutionized the way education institutions manage their data and systems. Cloud-based learning management systems (LMS) are widely used in the education industry to deliver online courses, assessments, and other educational resources. Cloud-based LMS enables educators to create and deliver personalized learning experiences to students from anywhere, on any device. Additionally, cloud-based collaboration tools are used to facilitate communication and collaboration between educators, students, and administrators.
4.Retail:
- Cloud computing is being used in the retail industry to manage inventory, process transactions, and provide personalized customer experiences. Retailers are using cloud-based point-of-sale systems to manage their sales data, track inventory levels, and process transactions in real-time. Cloud computing is also being used to personalize customer experiences by analyzing customer data and providing targeted recommendations and promotions.
5.Manufacturing:
- Cloud computing is being used in the manufacturing industry to manage production processes, improve supply chain management, and reduce costs. Manufacturing companies are using cloud-based tools to manage their production lines, track inventory levels, and monitor quality control. Cloud computing is also being used to optimize supply chain management by providing real-time visibility into inventory levels, shipping status, and delivery times.
5.Blockchain Technology: Revolutionizing Data Security and Digital Transactions
Explanation of blockchain and its components
Blockchain is a digital ledger technology that allows for secure, transparent, and decentralized record-keeping. It is essentially a database that is distributed across a network of computers, where each participant has a copy of the same database. Each transaction or record that is added to the blockchain is verified and stored in a secure and immutable way.

There are four main components of a blockchain:
- Distributed network: A blockchain is a distributed network of computers that work together to validate and store transactions. Each computer in the network has a copy of the same database, which is updated whenever a new transaction is added to the blockchain.
- Blocks:A blockchain consists of blocks that contain transactions or records. Each block is linked to the previous block, creating a chain of blocks (hence the name blockchain). The linking of blocks is done through a cryptographic hash function, which ensures the security and immutability of the blockchain.
- Consensus mechanism:In a blockchain network, participants must agree on the validity of transactions before they are added to the blockchain. This is done through a consensus mechanism, which ensures that all participants in the network are in agreement before a transaction is recorded on the blockchain. There are various consensus mechanisms, such as proof of work, proof of stake, and delegated proof of stake.
- Cryptography:Cryptography is used to secure the blockchain by creating digital signatures that verify the identity of the participants and ensure the integrity of the transactions. Each transaction on the blockchain is encrypted with a private key, which is only known to the owner of the transaction. This ensures that only the owner of the transaction can access and modify it.
Overall, blockchain technology offers a secure and transparent way of storing and verifying data, which has potential applications in a wide range of industries such as finance, healthcare, and supply chain management.
.Use cases of blockchain beyond cryptocurrencies (e.g., supply chain management, voting systems)
Blockchain technology has several use cases beyond cryptocurrencies. Here are some examples:
- Supply chain management:Blockchain technology can be used to create a transparent and secure supply chain management system. By recording each step of the supply chain process on the blockchain, companies can ensure that their products are authentic, and their suppliers are meeting their obligations. For example, Walmart is using blockchain technology to track the origin of produce, ensuring its freshness and safety.
- Voting systems:Blockchain technology can be used to create secure and transparent voting systems. By recording each vote on the blockchain, voters can be sure that their vote is being counted correctly, and the results are tamper-proof. Blockchain-based voting systems have the potential to eliminate voter fraud and improve voter turnout.
- Healthcare:Blockchain technology can be used to create secure and transparent electronic health records (EHRs). By recording each patient’s medical history on the blockchain, healthcare providers can ensure that the data is accurate and up-to-date. This can improve patient outcomes by allowing healthcare providers to make more informed decisions about patient care.
- Real estate:Blockchain technology can be used to create a transparent and secure real estate ownership registry. By recording each real estate transaction on the blockchain, buyers and sellers can be sure that the ownership records are accurate and up-to-date. This can reduce the risk of fraud and streamline the buying and selling process.
- Intellectual property:Blockchain technology can be used to create a secure and transparent system for registering and protecting intellectual property. By recording each registration on the blockchain, creators can be sure that their work is protected and that they are receiving proper compensation for their creations. This can reduce the risk of piracy and encourage innovation.
Overall, blockchain technology has the potential to transform many industries by providing secure and transparent record-keeping systems.
To know more about Blockchain Technology click on Link https://amateurs.co.in/2023/03/20/what-is-blockchain-technologyeverything-you-need-to-know-about/
6.Cybersecurity: Protecting Against Threats in the Digital Age
Overview of cybersecurity threats (e.g., malware, phishing)
Cybersecurity threats refer to any type of malicious activity or attack that aims to compromise the confidentiality, integrity, or availability of digital assets. These threats can come in various forms, such as malware, phishing, ransomware, DDoS attacks, and more. Here’s an overview of some of the most common cybersecurity threats:
- Malware:Malware is a type of software that is designed to damage, disrupt, or gain unauthorized access to computer systems or networks. This can include viruses, worms, Trojan horses, and spyware.
- Phishing:Phishing is a type of social engineering attack that involves tricking users into divulging sensitive information, such as usernames, passwords, and credit card numbers. Phishing attacks can come in various forms, such as email, text messages, or phone calls.
- Ransomware:Ransomware is a type of malware that encrypts a victim’s files, making them inaccessible until a ransom is paid. Ransomware attacks are usually delivered via phishing emails or malicious downloads.
- Distributed Denial of Service (DDoS) attacks:DDoS attacks are designed to overwhelm a website or network with traffic, making it inaccessible to users. These attacks can be launched by a single individual or a group of hackers using a botnet.
- Insider threats:Insider threats are attacks that come from within an organization. This can include employees or contractors who intentionally or unintentionally compromise sensitive information.
- Advanced Persistent Threats (APTs):APTs are sophisticated attacks that are carried out by skilled hackers who target a specific organization or individual over a prolonged period of time. These attacks are designed to remain undetected for as long as possible.
To protect against these threats, it’s important to implement a range of cybersecurity measures, such as using anti-malware software, encrypting sensitive data, and training employees on how to spot phishing scams.
Best practices for cybersecurity (e.g., password management, data encryption)
Effective cybersecurity practices are essential for protecting against cyber threats. Here are some best practices for cybersecurity:
- Use strong and unique passwords:Passwords are the first line of defense against cyber threats, so it’s important to use strong and unique passwords for every account. Passwords should be at least 12 characters long and include a mix of uppercase and lowercase letters, numbers, and symbols. Using a password manager can help you create and manage strong passwords.
- Enable two-factor authentication:Two-factor authentication adds an extra layer of security by requiring users to provide a second form of identification, such as a code sent to their phone, in addition to their password.
- Keep software up-to-date: Hackers often exploit vulnerabilities in outdated software to gain access to systems. Keeping software up-to-date with the latest security patches can help protect against these vulnerabilities.
- Use encryption:Encryption is the process of encoding data so that it can only be read by authorized parties. Using encryption for sensitive data can help protect against data breaches.
- Use a virtual private network (VPN):A VPN encrypts internet traffic and routes it through a secure server, making it more difficult for hackers to intercept. Using a VPN can help protect against cyber threats, especially when using public Wi-Fi.
- Back up data regularly:Regularly backing up data can help ensure that data is not lost in the event of a cyber attack or system failure.
- Train employees on cybersecurity best practices: Employees are often the weakest link in cybersecurity, so it’s important to provide regular training on cybersecurity bestpractices, such as how to spot phishing scams, how to use passwords securely, and how to identify potential cyber threats.
By implementing these cybersecurity best practices, individuals and organizations can significantly reduce their risk of falling victim to cyber attacks.

Future of cybersecurity and emerging technologies
The future of cybersecurity is closely tied to emerging technologies, as new technologies bring new cybersecurity threats and challenges. Here are some of the emerging technologies that are likely to shape the future of cybersecurity:
- Artificial Intelligence (AI):AI has the potential to transform cybersecurity by enabling more efficient and effective threat detection and response. AI-powered systems can analyzevast amounts of data to identify patterns and anomalies, helping to detect and respond to cyber threats in real-time.
- Internet of Things (IoT):IoT devices, such as smart home appliances and wearables, are becoming increasingly popular and connected. However, these devices often have weak security measures, making them vulnerable to cyber attacks. As the number of IoT devices continues to grow, securing them will become an increasingly important challenge for cybersecurity.
- Blockchain: Blockchain is a decentralized ledger technology that is used for secure transactions. Its use in cybersecurity can help provide secure and transparent storage and transmission of sensitive data.
- Quantum computing:Quantum computing has the potential to break many of the encryption methods used to protect sensitive data. As quantum computing becomes more powerful, new encryption methods will need to be developed to keep pace.
- Cloud computing:Cloud computing has revolutionized the way that organizations store and process data. However, it also brings new cybersecurity challenges, such as protecting cloud-based data from cyber threats.
To address these emerging cybersecurity challenges, organizations will need to invest in new technologies and cybersecurity measures. This includes developing new security protocols and standards, training employees on cybersecurity best practices, and investing in cybersecurity solutions that leverage emerging technologies like AI and blockchain. The cybersecurity landscape will continue to evolve rapidly, and organizations that stay ahead of the curve will be better equipped to protect against emerging cyber threats.
7.Conclusion: The Future of Information Technology and Its Impact on Society
The future of information technology (IT) is likely to be characterized by continued innovation and advancements in areas such as artificial intelligence, cloud computing, and the Internet of Things (IoT). These technologies have the potential to significantly impact society in a variety of ways, including:
- Increased automation:The increasing use of AI and robotics in industries such as manufacturing, healthcare, and transportation is likely to lead to increased automation of many jobs. This has the potential to increase productivity and efficiency, but may also result in job displacement for some workers.
- Enhanced communication and collaboration:Cloud-based platforms and collaboration tools are making it easier for people to work together remotely and across different geographies. This has the potential to increase productivity and reduce costs, but may also change the way we work and interact with others.
- Improved healthcare:Advances in healthcare IT, such as electronic health records and telemedicine, are likely to improve patient outcomes and reduce costs. This could lead to increased access to healthcare services and improved health outcomes for people around the world.
- Increased cybersecurity risks:As IT becomes more integrated into every aspect of our lives, the risks associated with cyber attacks and data breaches are likely to increase. This will require continued investment in cybersecurity measures and increased awareness among individuals and organizations.
- Greater personalization:Advances in AI and big data are making it possible to personalize products and services to individual preferences and needs. This could lead to more customized and efficient experiences for consumers, but may also raise concerns about privacy and data security.
Overall, the future of IT is likely to bring both opportunities and challenges for society. As we continue to innovate and develop new technologies, it will be important to consider the potential impacts on individuals and communities, and to work to address any negative consequences.

[…] to know about information technology and its division please click on link https://amateurs.co.in/2023/03/23/the-power-of-information-technology/ […]
[…] Unleashing the Power of Artificial Intelligence: Enhancing Society with its Positive Impact and Benefits “The Ultimate Guide to Machine Learning: Everything You Need to Know” “From AI to Cybersecurity: The Unstoppable Evolution of Information Technology” […]
[…] What is Internet of Things (IoT)? -“Discovering the Advantages and Potential of IoT Technology: An In-Depth Exploration Unleashing the Power of Artificial Intelligence: Enhancing Society with its Positive Impact and Benefits “The Ultimate Guide to Machine Learning: Everything You Need to Know” “From AI to Cybersecurity: The Unstoppable Evolution of Information Technology” […]